Strategic Arts and Sciences Alliance
The Brand Name of the Media Revolution

|
Idiosyntactix Strategic Arts and Sciences Alliance The Brand Name of the Media Revolution |

|
[library]
Threat CharacteristicsDefensive Information Warfare
Threat Characteristics
As can been seen from the series of graphical depictions of the threat topology presented above, the threat we face is multidimensional, somewhat messy and, with respect to the consequences of information attacks, can behave in a chaotic manner. The dynamic and interactive nature of the threat makes defending against attacks all the more challenging.
Attackers and defenders are locked in an ongoing battle of wits and resources as depicted in Figure 7, Threat Dynamics. Unfortunately, the attackers possess some inherent advantages. For example, the attacker can pick the time, place, medium, and method of the attack. The technology edge also goes to the attacker, for it is very difficult to develop perfect defenses at an affordable cost. Therefore, there will always be "holes." Which ones will be exploited are unknown until attacks occur, thus the offense usually is one step ahead of the defense. Those who choose to orchestrate coordinated attacks on infrastructure also have the advantage that comes from being able to control their attack more easily than can a number of loosely coupled defenders.
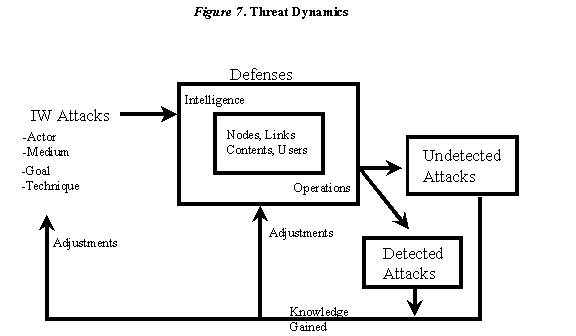
In any event this is a learning environment for both attackers and defendersùa dynamic one at that. In this organic environment, attackers learn from undetected attacks, whether successful or not, while both sides learn from detected attacks, whether successful or not. Both attackers and defenders make adjustments and the "game" continues.
This aspect of the threat means that defense is not a one time thing. It must be a continuous activity. It also means that collection and analysis of information about attacks is vital to maintaining parity with attackers. Finally, it means that defenders must be proactive and undertake efforts designed to anticipate methods of attack so that timely defenses can be developed.
IW-D Considerations
The problem of how best to defend against a variety of potential digital information attacks is exacerbated by the following three characteristics of the problem: our inability to develop a simple relationship between a type of attack or threat and an organization, the essentially non-linear relationship between outcome and value, and the fact that key variables are not within our control.
Being able to decompose a problem often helps us to make progress, at least on some fronts, by facilitating the delegation of either functional or jurisdictional responsibility along organizational lines. As we have seen, the problem of IW-D resists decomposition along organizational lines. This is because there is a weak mapping between threat and organization from two perspectives. First, the organizational target of the attack is weakly related to the threat topology, that is, an attack on a given organization may result in a set of consequences that span the threat spectrum. Second, there is no clean mapping between organizational responsibility and the threat topology. This is particularly true of the area identified as Potentially Strategic.
It is always easier to solve problems with well-behaved or predictable objective functions or measures of value. As we have seen, the IW-D problem has situations where the relationship between events and variables behave in a chaotic manner. This introduces a large dose of uncertainty into the equation.
If these first two characteristics of the IW-D problem did not present significant challenges in and of themselves, we are also faced with the fact that some of the key variables that have an influence on outcomes and the values of these outcomes are only partially controllable. For example, each of the following variables, if fully controllable, could significantly either reduce the number or severity of attacks and/or the impact of the attacks: proliferation of technology, level of awareness and training of personnel, availability of computer expertise, system defenses, and public perceptions.
We have come to the end of the discussion of the nature of the problem and its characteristics that will drive the search for a solution. Next, a proposed solution approach is presented and discussed.
.
.
.
[library]
.
.
.
![]()
![]()
.
.
.
![]()