Strategic Arts and Sciences Alliance
The Brand Name of the Media Revolution

|
Idiosyntactix Strategic Arts and Sciences Alliance The Brand Name of the Media Revolution |

|
[library]
Proposed IW-D StrategyDefensive Information Warfare
Proposed IW-D Strategy
The proposed solution to IW suggested here is a "Defense-in-Depth" strategy, a strategy that involves a series of successively stronger or "higher" defensive barriers that work together to decompose the spectrum of threats into manageable pieces. While implementing this concept still involves considerable challenges, it provides some structure for efforts to defend ourselves against information attacks.
Following a discussion of this IW-D strategy, the nature of a division of responsibility, some of the critical prerequisites for progress, key challenges that lie ahead, and the elements of an action plan for organizations with IW-D responsibilities will be addressed.
Defense-in-Depth
The proposed "defense-in-depth" strategy, depicted in Figure 8, consists conceptually of three lines of defense. Each line of defense is designed specifically to counter the threats associated with a particular region of the threat topology.
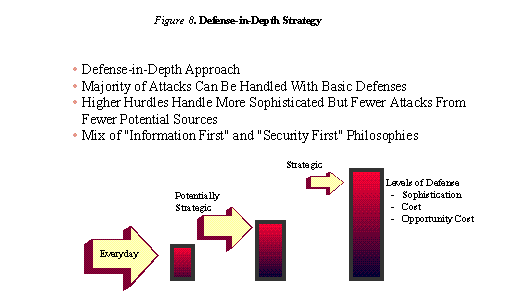
The first line of defense is to defend against Everyday attacks, which constituted most of the threat topology. Based upon the information available, the vast majority of these attacks can be handled with basic defenses.
The higher hurdles associated with the Potentially Strategic and Strategic attacks are then responsible for handling more sophisticated but far fewer attacks from fewer potential sources. For example, attacks with strategic implications would need to get through the first two lines of defense that should filter out all but the most skilled, resourced, and persistent adversaries. This means we can concentrate our intelligence and monitoring efforts on a smaller population, which in turn increases the chances of successful defense.
This defensive strategy also means that we can take different philosophical approaches with each line of defense depending on the nature of the threat. The two endpoints of the philosophical spectrum can be thought of as the "information first" and "security first" approaches. In the Everyday region of the threat topology our approach has been to emphasize access to information. In the Strategic region, we put security first by restricting access and connectivity to the point of degrading performance and efficiency.
Division of Responsibility
Figure 9 graphically depicts a suggested division of primary responsibility for IW-D between the public and private sectors as a function of the threat topology. The modifier "primary" is used to make the point that, despite the assignment of responsibility in a particular area to either the public or private sector, both public and private organizations have responsibilities in each area.
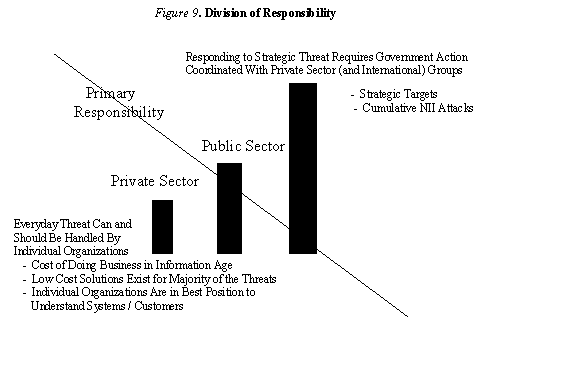
The topological regions associated with either Everyday or Strategic threats are the most straightforward. Primary responsibility for the everyday threat should be the responsibility of the private sector. Handling such threats is simply the cost of doing business in the Information Age. With the availability of relatively low-cost defenses against these threats, the burden placed on the private sector is affordable. Furthermore, organizations are clearly in the best position to understand their own systems and the needs and concerns of their customers.
Responding to strategic threats is clearly the job of the public sector, although an adequate defense will involve some coordination with private sector and international organizations, particularly when it comes to the region of the threat topology that contains threats associated with attacks on the national information infrastructure or other institutions providing vital services.
Where to assign primary responsibility for defenses against threats in the Potentially Strategic region of the threat topology is less clear. This area could be called a "zone of collaboration," where the public and private sectors need to work closely together to understand the threat and develop mechanisms designed to counter it.
Perspectives on Information Security
Efforts to achieve effective collaboration will need to overcome the understandably different perspectives that organizations bring to the table.
Commercial organizations traditionally treat events such as Everyday attacks as simply a cost of doing business not significantly different than pilferage euphemistically referred to as inventory "shrinkage." Countermeasures have a definite expected value and are employed when their costs are less than their expected value. Private sector organizations traditionally respond to relatively low probability events with potentially large costs by either purchasing insurance or providing self-insurance.
The perspective on information security taken by organizations entrusted with information and systems deemed vital to our national security is quite different. Unlike many information attacks on private sector systems, the cost of a breech in security of national security information can not easily be determined. Overshadowing the actual costs of a particular incident is the fact that the very protection of the integrity of national security information and the systems that handle it is considered to have intrinsic value in and of itself. Risk avoidance is the ingrained response in these situations.
Given the nature of the IW threat topology, national and private sector information security are now inexorably intertwined. Attacks on the national or global information infrastructure can seriously affect private sector organizations and attacks on key private sector organizations that provide vital services have definite national security implications. These situations are contained in the Potentially Strategic region of the threat topology.
It is proposed that, in this region, rather than take a simple "dollars and cents" approach as in the Everyday region or a risk avoidance approach as taken in the Strategic region, we should take a collective risk management approach. This is clearly an area which requires defenses to be closely coordinated.
.
.
.
[library]
.
.
.
![]()
![]()
.
.
.
![]()