Strategic Arts and Sciences Alliance
The Brand Name of the Media Revolution

|
Idiosyntactix Strategic Arts and Sciences Alliance The Brand Name of the Media Revolution |

|
[library]
Threat TopologyDefensive Information Warfare
Threat Topology
A graphical depiction of the threat topology is presented in Figure 2, The Threat Space. The irregular nature of the space is meant to indicate that its boundaries are not well defined. Nevertheless, one can group threats in order of the seriousness of their consequences (from left to right). The consequences associated with a failure to counter a specific attack range, on the one hand, from isolated and limited consequences to, on the other hand, consequences of catastrophic proportions.
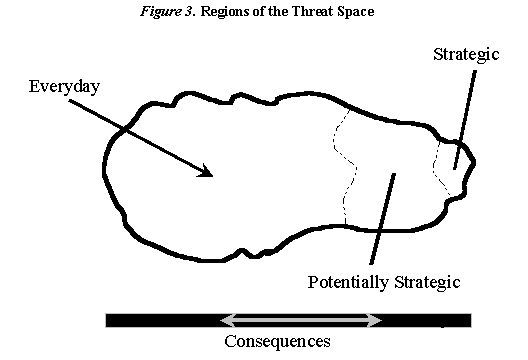
In a series of pictures, Figures 3 through 6, different aspects of the threat topology are depicted. In Figure 3, the Threat Space is divided into three areas. On the left side of the space we can group the vast majority of the threats that occur everyday. These Everyday threats, while exacting a certain price, do not pose a threat to our national security. On the right hand side of the threat spectrum is a small area that represents those strategic threats having national security implications. The third area contains threats that may have national security implications. These Potentially Strategic threats represent a particularly difficult challenge.
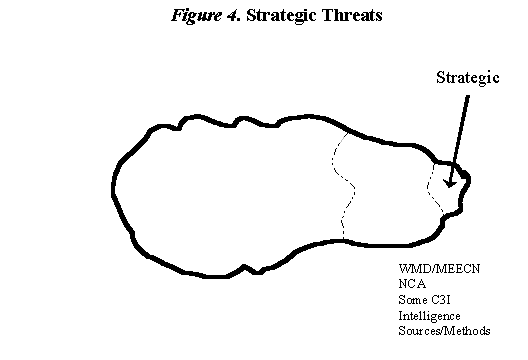
There are a relatively small number of threats that most everyone would agree have strategic implications (Figure 4) and must be defended against with considerable vigor. Attacks against our systems that control and safeguard weapons of mass destruction (WMD) and our minimum essential emergency communication network (MEECN) clearly fall into this category. Others that fall into this category would include the information and communication systems associated with the National Command Authority (NCA), some of our command, control, communications and intelligence (C3I) systems, and some of our intelligence systems, particularly information regarding sources and methods. A review of other Government information and information systems would result in additional information and systems that should be added to this list.
Beyond those sets of threats that clearly fall into either the Everyday or Strategic categories, there are classes of threats that span the threat spectrum.
Attacks on our national, or for that matter international, infrastructure (Figure 5) do not fall neatly into one area of the threat topology but in fact populate all three classes of threat. These attacks on our public safety, energy, financial, and communications systems and services have different implications and consequences depending on the specific nature of the attacks and the circumstances surrounding the attack.
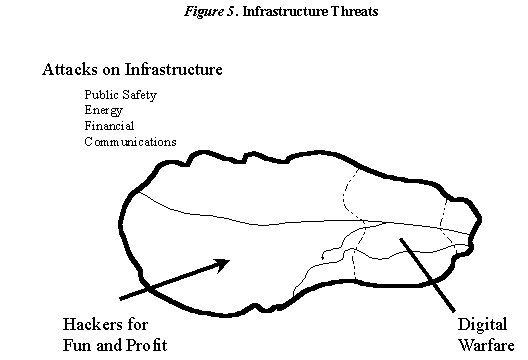
The vast majority of attacks on infrastructure are by hackers whose motives run the full gamut from financial motives, to having some fun, or to more serious forms of antisocial behavior. While some of these attacks may have serious consequences in the form of significant losses of data, interrupted services, or stolen assets or services, only a small number of these lone perpetrator attacks are likely to have potential strategic consequences. This is not to say that it is impossible that some set of circumstances would result in the snowballing of one of these hacker attacks into a national security concern, but rather that this outcome is unlikely.
However, infrastructure attacks can be quite serious if they are well planned and coordinated. Arguably this would require an adversary with seriousness of purpose and with some sophistication and organization. This kind of attack would be better named digital warfare rather than be included as part of the group referred to as hacker attacks. Depending on the level of sophistication of a digital warfare operation, its consequences could range from a "high-end" hacker attack to an attack with strategic consequences.
A key point to be made involves the chaotic nature of the transition between topological boundaries for infrastructure attacks. Chaotic behavior involves a non-linear relationship between input and output where prediction becomes extremely difficult if not impossible. Two distinct scenarios serve to illustrate the chaotic nature of infrastructure attacks. In the first case, a particular infrastructure attack may trigger a series of proximate consequences that are difficult to predict and that greatly magnify the effects of the attack. In the second case, a series of attacks will exhibit chaotic behavior when the sum of their consequences can not be determined by adding up their individual consequences, or when their cumulative effect far exceeds the sum of the individual effects of a series of independent events. These are not uncommon patterns. Valid scientific disciplines of complexity, catastrophe, and complexity theory have been developed because these patterns occur throughout nature.
It is much the same story for attacks on commercial targets, depicted in Figure 6. In the Everyday category are attacks that amount to Information Age versions of fraud and theftùa continuation of white collar crime and a transformation of some more violent crime into a non-physical form. As Dr. Horton (PDASD (C3I)) has pointed out, one of the more notorious bank robbers of the 20th century, when asked why he robbed banks (given that they were often so well defended), was purported to remark, "that's where the money is." Well, digital money (assets and services) is where the money is in the Information Age.

As with attacks on infrastructure, attacks on commercial targets can range from Everyday threats to Strategic ones depending on the circumstances. Attacks on commercial targets by competing organizations usually do not target money directly, but rather target vital information (e.g., trade secrets) and have the potential for more serious consequences than isolated thefts or embezzlements. These attacks, in the form of commercial espionage, have Potentially Strategic consequences, particularly when key industries are targeted by foreign companies.
Commercial espionage turns into economic war which could have Strategic consequences when it involves concerted efforts by state actors, international organizations, or other foreign-controlled groups.
.
.
.
[library]
.
.
.
![]()
![]()
.
.
.
![]()