Strategic Arts and Sciences Alliance
The Brand Name of the Media Revolution

|
Idiosyntactix Strategic Arts and Sciences Alliance The Brand Name of the Media Revolution |

|
[library]
Building a Defense-in-DepthDefensive Information Warfare
Building a Defense-in-Depth
Our ability to defend individual systems and the information they handle is the foundation of any IW-D strategy or approach. In order to achieve the requisite level of defenses, we need to 1) revise our approach to system design and acquisition, 2) understand the dimensions of defense, and 3) support the development of critical enabling technologies.
System Design and Acquisition
The current trend in designing systems is to provide vastly increased access to increasing amounts of information at all levels of an organization and to provide for more external connectivity. We in government are joining the move to separate the flow of information from the management or command structure. Our new approach to information systems involves "reach back," that is, individuals are not "pushed" information but rather "pull" the information they require from distributed databases. In response to the sheer amount of information available, more and more sophisticated presentations (displays) are being developed. Driven by the reduced life cycle of information technology and shrinking budgets, we are becoming more and more reliant on commercial-off-the-shelf (COTS) equipment and software. These trends make it more and more difficult to ensure the integrity of information or recognize when it has been compromised.
If we are to build the level of defenses to IW attacks we need and provide users with the level of assurance required to give them confidence in their systems, we need some changes in our approach to system design and acquisition. For a number of reasons, not the last of which is security, we need to focus more on providing quality information, that is on moving up the "data-information-understanding-knowledge" continuum. In evaluating system designs and in setting standards for systems to meet, we need to augment the current set of measures of merit (MOMs) for information. In addition to attributes such as timeliness and accuracy, we also need to focus on authenticity, integrity, and availability.
Connectivity is important to achieving the levels of functionality desired, but increased emphasis on secure interoperability is needed to achieve IW-D objectives. Fixing and patching systems and installing new releases offer many opportunities to bypass or disable system defenses. Operations and Maintenance (O&M) activities also provide opportunities to prevent intrusions and strengthen system defenses. System operators and software maintenance engineers are often the least experienced and lowest paid in their professions. They also typically receive the least training. Given the critical nature of O&M for maintaining system defenses, O&M practices need to be reviewed.
Dimensions of Defense
Defense is a function of more than design and software quality assurance. It has many dimensions, some of which are depicted in Figure 10. Each of these dimensions needs to be considered for each specific system and set of circumstances.
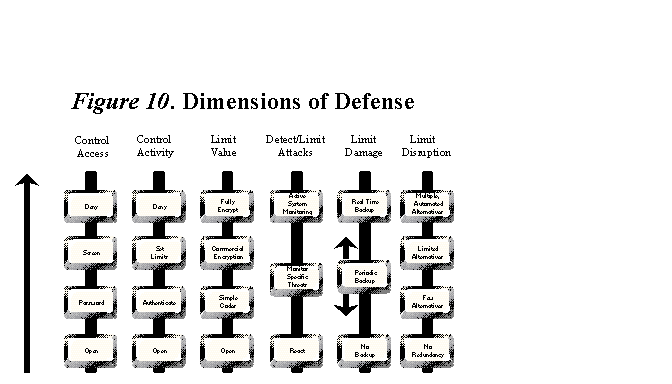
In addition to how a system is designed, these dimensions of defense include system operations, methods, and procedures employed to limit the attractiveness of an attack and/or the consequences of an attack. Figure 10 presents some of the dimensions of defense that need to be considered in constructing and "tuning" each system to its unique set of circumstances. Each dimension offers a range of choices that provides either more or less protection. More protection always comes at a price (although surprisingly the price may be quite low, particularly when compared with the security gains that can be achieved). Achieving higher levels of protection either actually costs more to build into a system or exacts a cost in terms of operating overhead or in loss of functionality.
Critical Technologies
Building defenses into systems presumes we have the means to do so. Many of the defensive capabilities we currently have are not adequate for certain known levels or types of attacks, not to mention technically feasible but undocumented attacks. The following are some areas in which we could use some advances in technology.
Real-time intrusion detection is clearly a key element in any set of defenses. Our ability to detect, in real time, intrusions into our systems and the identity of the intruder is currently very limited. In does not take very long to carry out an information attack. Damage can occur in an instant. Clearly an automated capability to respond to an intrusion that can prevent or limit the damage would be highly desirable.
Given our increasing reliance on COTS, we need ways to cost-effectively make sure that the software we buy does what we want it to and only what we want it to. Any Information Age organization buys millions of lines of code each year whose exact origins are not known with any degree of confidence. Automated tools for performing quality assurance (QA) and for verifying and validating (V&V) the code would be an immense help.
Knowing for sure that data were not altered or compromised and that the source of a piece of data or a message was verified would go a long way in the effort to combat certain types of IW attacks. More work needs to be done to provide cost-effective data and source authentication.
.
.
.
[library]
.
.
.
![]()
![]()
.
.
.
![]()